 Use of historical methods The Five Gospels
Use of historical methods The Five Gospels lists seven bases for the modern critical scholarship of Jesus. These "pillars" have developed since the end of the 18th century.
While some of these pillars are noncontroversial, some scholars of the historical Jesus follow
Albert Schweitzer. First, since the 1960s, the gospel references to the coming
Son of Man have been sometimes viewed as insertions by the early Christian community. Second, many scholars came to see Jesus'
kingdom of God as a present reality, a "
realized eschatology", rather than an imminent end of the world. The apocalyptic elements attributed to Jesus, according to
The Five Gospels, come from
John the Baptist and the
early Christian community (p. 4).
Distinguishing between historical Jesus and the Christ of faith (see
Hermann Samuel Reimarus,
David Strauss).
Recognizing the synoptic gospels as more historically accurate than John (19th century German tradition, see
higher criticism).
The
priority of Mark before Matthew and Luke (by 1900)
Identification of the
Q document (by 1900)
Rejection of eschatological (apocalyptic) Jesus (1970s and 1980s).
Distinction between oral and written culture
Reversal of burden of proof from those who consider gospel content to be ahistorical to those who consider it historical.
"Seven pillars of scholarly wisdom" The Seminar began by translating the gospels into modern
American English, producing the "Scholars Version," (to be found in
The Five Gospels). This translation uses current colloquialisms and contemporary phrasing in an effort to provide a contemporary sense of the gospel authors' styles, if not their literal words. The goal was to let the reader hear the message as a first-century listener might have. The translators avoided other translations' archaic, literal translation of the text, or a superficial update of it. For example, they translate "woe to you" as "damn you" because it sounds like something someone today would really say. The authors of
The Five Gospels allege that some other gospel translations have attempted to unify the language of the gospels, while they themselves have tried to preserve each author's distinct voice.
The Scholars translation The Jesus Seminar, like the translation committees who created the
King James Version and the
Revised Standard Version of the Bible and the
Novum Testamentum Graece, chose voting as the most efficient means of determining consensus in an assembled group. The system also lent itself to publicity, which the Seminar actively pursued.
The Fellows used a "bead system" to vote on the authenticity of about 500 statements and events. The color of the bead represented how sure the Fellow was that a saying or act was or was not authentic.
The consensus position was determined by the average weighted score, rather than by simple majority. This meant that all opinions were reflected in the decisions. The voting system means that the reader can second-guess each vote.
The Five Gospels defines not only the result of the vote (red, pink, gray, or black) but also how many polls were necessary to reach a conclusion (if any were necessary at all) and why various fellows chose to vote in different ways.
Attendees, however, did more than vote. They met semi-annually to debate the papers presented. Some verses required extensive debate and repeated votes.
Red beads – indicated the voter believed
Jesus did say the passage quoted, or something very much like the passage. (3 Points)
Pink beads – indicated the voter believed Jesus probably said something like the passage. (2 Points)
Grey beads – indicated the voter believed Jesus did not say the passage, but it contains Jesus' ideas. (1 Point)
Black beads – indicated the voter believed Jesus did not say the passage—it comes from later admirers or a different tradition. (0 Points)
Seminar proceedings The first findings of the Jesus Seminar were published in
1993 as
The Five Gospels: The Search for the Authentic Words of Jesus.
Sayings of Jesus Like other scholars of the historical Jesus, the Jesus Seminar treats the gospels as fallible historical artifacts, containing both authentic and inauthentic material. Like their colleagues, the fellows used several criteria for determining whether a particular saying or story is authentic, including the criteria of
multiple attestation and
embarrassment. Among additional criteria used by the fellows are the following:
Orality: According to current estimates, the gospels weren't written until decades after Jesus' death. Parables, aphorisms, and stories were passed down orally (30 - 50 CE). The fellows judged whether a saying was a short, catchy pericope that could possibly survive intact from the speaker's death until decades later when it was first written down. If so, it's more likely to be authentic. For example, "
turn the other cheek."
Irony: Based on several important narrative parables (such as the
Parable of the Good Samaritan), the fellows decided that irony, reversal, and frustration of expectations were characteristic of Jesus' style. Does a pericope present opposites or impossibilities? If it does, it's more likely to be authentic. For example, "
love your enemies."
Trust in God: A long discourse attested in three gospels has Jesus telling his listeners not to fret but to trust in the Father. Fellows looked for this theme in other sayings they deemed authentic. For example, "
Ask -- it'll be given to you."
Criteria for authenticity The seminar looked for several characteristics that, in their judgment, identified a saying as inauthentic, including self-reference, leadership issues, and apocalyptic themes.
Self-reference: Does the text have Jesus referring to himself? For example, "I am the way, and I am the truth, and I am life" (
John 14:1-14).
Framing Material: Are the verses used to introduce, explain, or frame other material, which might itself be authentic? For example, in Luke, the "red" parable of the good samaritan is framed by scenes about Jesus telling the parable, and the seminar deemed Jesus' framing words in these scenes to be "black."
Community Issues: Do the verses refer to the concerns of the early Christian community, such as instructions for missionaries or issues of leadership? For example, Peter as "the rock" on which Jesus builds his church (
Matthew 16:17-19).
Theological Agenda: Do the verses support an opinion or outlook that is unique to the gospel, possibly indicating
redactor bias? For example, the prophecy of the sheep and the goats (
Matthew 25:31-46) was voted black because the fellows saw it as representing Matthew's agenda of speaking out against unworthy members of the Christian community.
Criteria for inauthenticity The Red sayings (with % indicating the weighted average of those in agreement), given in the Seminar's own "Scholar's Version" translation, are:
1.
Turn the other cheek (92%):
Mt 5:39,
Lk6:29a
2.
Coat & shirt: Mt5:40 (92%), Lk6:29b (90%)
3.
Congratulations, poor!: Lk6:20b (91%),
Th54 (90%), Mt5:3 (63%)
4.
Second mile (90%): Mt5:41
5.
Love your enemies: Lk6:27b (84%), Mt5:44b (77%), Lk6:32,35a (56%) (compare to
black rated "Pray for your enemies":
POxy1224 6:1a;
Didache 1:3;
Poly-Phil 12:3; and "Love one another":
John 13:34-35,
Romans 13:8,
1 Peter 1:22)
6.
Leaven: Lk13:20–21 (83%), Mt13:33 (83%), Th96:1–2 (65%)
7.
Emperor & God (82%): Th100:2b–3,
Mk12:17b, Lk20:25b, Mt22:21c (also
Egerton Gospel 3:1-6)
8.
Give to beggars (81%): Lk6:30a, Mt5:42a, Didache1:5a
9.
Good Samaritan (81%): Lk10:30–35
10.
Congrats, hungry!: Lk6:21a (79%), Mt5:6 (59%), Th69:2 (53%)
11.
Congrats, sad!: Lk6:21b (79%), Mt5:4 (73%)
12.
Shrewd manager (77%): Lk16:1–8a
13.
Vineyard laborers (77%): Mt20:1–15
14.
Abba, Father (77%): Mt6:9b, Lk11:2c
15.
The Mustard Seed : Th20:2–4 (76%), Mk4:30–32 (74%), Lk13:18–19 (69%), Mt13:31–32 (67%)
Authentic sayings, as determined by the seminar The top 15 (of 75) Pink sayings are:
16.
On anxieties, don't fret (75%): Th36, Lk12:22–23, Mt6:25
17.
Lost Coin (75%): Lk15:8–9
18.
Foxes have dens: Lk9:58 (74%), Mt8:20 (74%), Th86 (67%)
19.
No respect at home: Th31:1 (74%), Lk4:24(71%),
Jn4:44 (67%), Mt13:57 (60%), Mk6:4 (58%)
20.
Friend at midnight (72%): Lk11:5–8
21.
Two masters : Lk16:13a, Mt6:24a (72%); Th47:2 (65%)
22.
Treasure: Mt13:44 (71%), Th109 (54%)
23.
Lost sheep: Lk15:4–6 (70%), Mt18:12–13 (67%), Th107 (48%)
24.
What goes in: Mk7:14–15 (70%), Th14:5 (67%), Mt15:10-11 (63%)
25.
Corrupt judge (70%): Lk18:2–5
26.
Prodigal son (70%): Lk15:11–32
27. Leave the dead (see also
But to bring a sword,
Nazirite): Mt8:22 (70%), Lk9:59–60 (69%)
28.
Castration for Heaven (see also
Origen,
Antithesis of the Law) (70%): Mt19:12a
29.
By their fruit (69%) (see
Antinomianism): Mt7:16b, Th45:1a, Lk6:44b (56%)
30.
The dinner party, The wedding celebration: Th64:1–11 (69%), Lk14:16-23 (56%), Mt22:2-13 (26%)
Some probably authentic sayings, as determined by the seminar The Seminar concluded that of the various statements in the "five gospels" attributed to Jesus, only about 18% of them were likely uttered by Jesus himself (red or pink). The
Gospel of John fared worse than the
synoptic gospels, with nearly all its passages attributed to Jesus being judged inauthentic. The
Gospel of Thomas includes just two unique sayings that the seminar attributes to Jesus:
the empty jar (97) and
the assassin (98). Every other probably-authentic or authentic saying has parallels in the synoptics.
Overall reliability of the five gospels The gospels use the terms
gehenna and
hades for places of fiery punishment and death. The fellows rated Jesus' references to gehenna and hades as gray at best, often black. Some such references (such as the parable of
Lazarus and Dives) have features that the fellows might regard as authentic, such as dramatic reversals of fortune. These received gray designations. The fellows regarded other references as inventions of early Christians responding to those who rejected Jesus' message or to "false" Christians within the community.
Gehenna and Hades The Jesus Seminar rated various beatitudes as red, pink, gray, and black.
To analyze the beatitudes, they first innovated a nonliteral translation for the formula "blessed are," as in "Blessed are the poor." Modern readers are familiar enough with the beatitudes that this construction doesn't shock or surprise, as the original sayings allegedly did. As the modern equivalent, the Scholar's Version uses "Congratulations!"
Three beatitudes are "paradoxical" and doubly attested. They are rated red (authentic) as they appear in Luke 6:20-21.
Congratulations, you poor! God's domain belongs to you. Congratulations, you hungry! You will have a feast. Congratulations, you who weep now! You will laugh.
These beatitudes feature the dramatic presentation and reversal of expectations that the seminar regards as characteristic of Jesus.
The beatitude for those persecuted in Jesus' name might trace back to Jesus as a beatitude for those who suffer, the fellows decided, but in its final form the saying represents concerns of the Christian community rather than Jesus' message. Thus it received a gray rating.
Matthew's version of the three authentic beatitudes were rated pink. The author has spiritualized two of them, so that they now refer to the poor "in spirit" and to those who hunger "and thirst for justice." Matthew also includes beatitudes for the meek, the merciful, the pure of heart, and peace-makers. These beatitudes have no second attestation, lack irony, and received a black rating.
Example: the beatitudes In 1998 the Jesus Seminar published
The Acts of Jesus: The Search for the Authentic Deeds of Jesus. According to the front flap summary: "Through rigorous research and debate, they have combed the gospels for evidence of the man behind the myths. The figure they have discovered is very different from the icon of traditional Christianity."
According to the Jesus Seminar:
The 10 authentic ("red") acts of Jesus are:
The 19 "pink" acts ("a close approximation of what Jesus did") are:
Also 1 red "summary and setting" (not a saying or action):
Women companions of Jesus:
Luke 8:1-3.
Jesus of Nazareth was
born during the reign of
Herod the Great.
His mother's name was
Mary, and he had a human father whose name may not have been
Joseph.
Jesus was born in
Nazareth, not in
Bethlehem.
Jesus was an itinerant
sage who shared meals with social outcasts.
Jesus practiced healing without the use of ancient medicine or magic, relieving afflictions we now consider
psychosomatic.
He did not
walk on water,
feed the multitude with loaves and fishes,
change water into wine or
raise Lazarus from the dead.
Jesus was
arrested in Jerusalem and
crucified by the
Romans.
He was executed as a public nuisance, not for claiming to be the
Son of God.
The
empty tomb is a fiction -- Jesus was not
raised bodily from the dead.
Belief in the
resurrection is based on the
visionary experiences of
Paul,
Peter and
Mary.
The Beelzebul controversy:
Luke 11:15-17 A voice in the wilderness:
Mark 1:1-8,
Matt 3:1-12,
Luke 3:1-20,
Gospel of the Ebionites 1
John baptizes Jesus:
Mark 1:9-11,
Matt 3:13-17,
Luke 3:21-22, Gospel of the Ebionites 4
Jesus proclaims the good news:
Mark 1:14-15 Dining with sinners:
Mark 2:15-17,
Matt 9:10-13,
Oxyrhynchus Gospels 1224 5:1-2
Herod beheads John:
Mark 6:14-29,
Matt 14:1-12,
Luke 9:7-9 Crucifixion: core event considered authentic but all gospel reports are "improbable or fictive" ("black")
The Death of Jesus: core event considered authentic but all gospel reports are "improbable or fictive" ("black")
The first list of appearances: Jesus appeared to
Cephas:
1Cor 15:3-5 Birth of Jesus: Jesus's parents were named Joseph and Mary: parts of
Matt 1:18-25 and
Luke 2:1-7 Peter's mother-in-law:
Mark 1:29-31,
Matt 8:14-15,
Luke 4:42-44 The leper:
Mark 1:40-45,
Matt 8:1-4,
Luke 5:12-16,
Egerton Gospel 2:1-4
Paralytic and four:
Mark 2:1-12,
Matt 9:1-8,
Luke 5:17-26 Call of Levi:
Mark 2:13-14,
Matt 9:9,
Luke 5:27-28, Gospel of the Ebionites 2:4
Sabbath observance:
Mark 2:23-28,
Matt 12:1-8,
Luke 6:1-5 Jesus' relatives come to get him:
Mark 3:20-21 True relatives:
Mark 3:31-35,
Matt 12:46-50, Thomas 99:1-3
Woman with a vaginal hemorrhage:
Mark 5:24-34,
Matt 9:20-22,
Luke 8:42-48 No respect at home:
Mark 6:1-6,
Matt 13:54-58 Eating with defiled hands:
Mark 7:1-13,
Matt 15:1-9 Demand for a sign:
Luke 11:29-30 The blind man of Bethsaida:
Mark 8:22-26 Blind Bartimaeus:
Mark 10:46-52,
Luke 18:35-43 Temple incident:
Mark 11:15-19,
Matt 21:12-17,
Luke 19:45-48 Emperor & God:
Mark 12:13-17,
Matt 22:15-22,
Luke 20:19-26, Thomas 100:1-4, Egerton 3:1-6
The arrest: core event not accurately recorded
Before the
high priest: core event not accurately recorded
Before the Council: core event not accurately recorded
Before Pilate: core event not accurately recorded
Acts of Jesus Arguably the single most telling criticism of the Jesus Seminar is that their "Criteria for In/Authenticity" create 'an eccentric Jesus who learned nothing from his own culture and made no impact on his followers'. go so far as to depict the Jesus Seminar as a tool of
Satan, meant to undermine Biblical beliefs.
the voting system is seriously flawed,
the criteria defining what constitutes red/pink/grey/black are inconsistent,
it was an error to exclude apocalyptic messages from Jesus' ministry,
the attempt to popularize Jesus research degraded the scholarly value of the effort,
the conclusions largely represent the premises of the fellows: 'Beware of finding a Jesus entirely congenial to you.' Funk et al., The Five Gospels;
only about 14 of the fellows are leading figures in New Testament scholarship, and
the fellows do not represent a fair cross-section of viewpoints.
Fellows of the Jesus Seminar Historicity of Jesus Liberal Christianity Two-source hypothesis
 Chicago School Classical liberalism Individualist anarchism Civil liberties Economic freedom Free markets Free trade Humanism Laissez-faire Liberty Individualism Non-aggression Private property Self-ownership Tax cuts Economic views History Movement Parties Theories of law Views of rights Criticism of libertarianism Libertarian Republican Libertarian Democrat The Austrian School, also known as the "Vienna School" or the "Psychological School", is a heterodox school of economic thought that advocates adherence to strict methodological individualism. As a result Austrians hold that the only valid economic theory is logically derived from basic principles of human action. Alongside the formal approach to theory, often called praxeology, the school has traditionally advocated an interpretive approach to history. The praxeological method allows for the discovery of economic laws valid for all human action, while the interpretive approach addresses specific historical events.
Chicago School Classical liberalism Individualist anarchism Civil liberties Economic freedom Free markets Free trade Humanism Laissez-faire Liberty Individualism Non-aggression Private property Self-ownership Tax cuts Economic views History Movement Parties Theories of law Views of rights Criticism of libertarianism Libertarian Republican Libertarian Democrat The Austrian School, also known as the "Vienna School" or the "Psychological School", is a heterodox school of economic thought that advocates adherence to strict methodological individualism. As a result Austrians hold that the only valid economic theory is logically derived from basic principles of human action. Alongside the formal approach to theory, often called praxeology, the school has traditionally advocated an interpretive approach to history. The praxeological method allows for the discovery of economic laws valid for all human action, while the interpretive approach addresses specific historical events.
 Description
Description Geography
Geography
 In the United States
In the United States History
History

 Electoral divisions
Electoral divisions
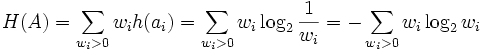
 [2].
[2]. could not be assigned code
could not be assigned code  , but instead should be assigned either
, but instead should be assigned either  or
or  . This is also known as the Hu-Tucker problem, after the authors of the paper presenting the first
. This is also known as the Hu-Tucker problem, after the authors of the paper presenting the first 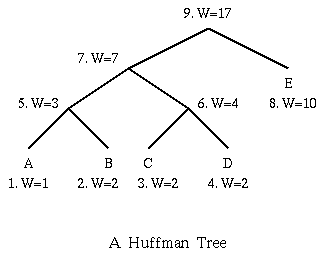 Applications
Applications Use of historical methods
Use of historical methods